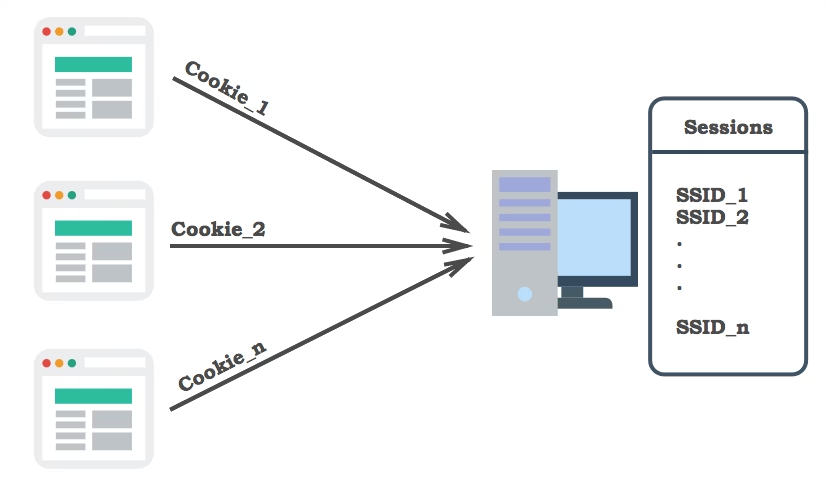
API Maturity Model
The Richardson Maturity Model (RMM) is a framework for evaluating the maturity of RESTful APIs. It was introduced by Leonard Richardson to classify APIs based on their adherence to REST principles. The model consists of four levels (0 to 3), where higher levels indicate a better alignment with RESTful architecture. Levels of the Richardson Maturity … Read more